I found the existing protocol flow diagram in the current OAuth spec..
OAuth Core 1.0
http://oauth.net/core/1.0/
..somewhat hard to follow. So I concocted three separate new ones using the so-called “swimlane” technique that I’m used to.
I posted these to the OAuth list a while back, and a few folks reposted them to their blogs, but no one has yet piped up to say I got anything wrong. But YMMV, there might be bugs in here.
FWIW, I’ve posted them below in case others find them useful. Also, I have them in a single file..
http://identitymeme.org/doc/draft-hodges-oauth-05-figures.txt
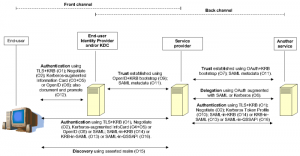
..also featuring OpenID and SAML Web Browser SSO Profile diagrams for comparison purposes. Note that in all things protocol, definitions of terms are essential in order to be able to effectively communicate and reason about protocols, so I’ve included key definitions from the OAuth spec in the file.
NOTE: fixed-pitch font required for viewing. Also, wordpress is obviously messing up the diagrams below, and they consequently look sorta lame, here on the blog. This site presently uses an old wordpress install, maybe this will help motivate me to upgrade it. In the meantime, check out the file linked-to above for the best viewing experience 😉
Fig 1: out-of-band consumer setup/config
photos.example.net
+----------+
| |
| OAuth |
| service |
printer.example.com | provider |
+---------+ | |
|developer| | Sys |
| of | | Admin |
| OAuth | | |
|consumer | | |
| | | [SP] |
+----+----+ +----+-----+
| |
| obtain Consumer Key |
| and Consumer Secret |
| [details unspec'd, |
| performed out-of- |
| band.] |
|--------------------->|
|< ---------------------|
| |
| |
Fig 2: "Web-based consumer"
The "consumer" is a website or other application that accesses
the Service Provider on behalf of the wielder (user) of the user agent
(UA is typically a browser, but could be some other app).
Steps 1.n. "Obtain Unauthorized Request Token"
2.n. "User Authorizes Request Token"
3.n. "Exchange Request Token for Access token"
4.n. UA accessing protected resources at SP
photos.example.net
+----------+
| |
| OAuth |
printer.example.com | Service |
+--------+ | Provider |
| | | |
| OAuth | |[protected|
|Consumer| |resources]|
+----+ | | | |
| UA | | [RP] | | [SP] |
+-+--+ +---+----+ +----+-----+
| | |
| 1.0. User Agent inter-| |
| acts with Consumer | |
| site [optional] | |
|< --------------------->| |
| | |
| | |
| | |
| 1.1. UA informs/directs |
| Consumer to do something |
| with a resource (e.g. | |
| a photo) at SP | |
|---------------------->| |
| | |
| | |
| | |
| | 1.2. Consumer attempts
| | accessing photo at SP|
| |--------------------->|
| | |
| | |
| | 1.3. SP replies with |
| | a HTTP 401 containing|
| | a "OAuth" www-authn |
| | header field |
| |< ---------------------|
| | |
| | |
| | 1.4. Consumer replies|
| | with a request for |
| | "unauthorized Request|
| | Token" (uRT) via POST|
| | to SP's "request token
| | URL" |
| |--------------------->|
| | |
| | |
| | 1.5. SP issues uRT & |
| | token secret to |
| | Consumer. |
| |< ---------------------|
| | |
| | |
| | |
| 2.0. Consumer redirects |
| UA to SP "User Author-| |
| ization URL" including| |
| the uRT. | |
+<- - - - - - - - - - - - | |
. | (indirected via UA) | |
. | | |
+-------------------------+--------------------->|
| | |
| | |
| | |
| | |
| 2.2. User authenticates with the Service |
| Provider (optional, methods vary, realization|
| is out of scope) |
|< ============================================>|
| 2.3. User grants or declines permission |
| for the Service Provider allow Consumer |
| access to the resource (e.g. photo). |
| | |
| | |
| | |
| | |
| 2.4. If permision granted, UA redirected back|
| to Consumer's "Callback URL", conveying the |
| uRT. | |
+< - - - - - - - - - - - - - - - - - - - - - - - -|
. | (indirected via UA) | |
. | | |
. | | |
+------------------------>| |
| | |
| | |
| |3.0. Consumer requests|
| |Access token, supplies|
| |uRT. |
| |--------------------->|
| | |
| | |
| | |
| |3.1. SP grants Access |
| | Token. |
| |< ---------------------|
| | |
| | |
| |4.x. Consumer uses the|
| |Access Token, Access |
| |Token Secret, Consumer|
| |Key, and Consumer Secret
| |to make authenticated |
| |request(s) to the Service
| |Provider. |
| |=====================>|
| | . |
| | . |
| | . |
| | |
Fig 3: “desktop-based consumer”
this is case where user is wielding some app that is both a UA and a Consumer.
+----------+
| |
| OAuth |
| service |
+--------+ | provider |
| | | |
|Desktop-| |[protected|
|based | |resources]|
|Consumer| | |
| | | |
| UA | | [SP] |
+-+------+ +----+-----+
| |
| 1. Consumer requests "unauthorized Request |
| Token (uRT)" with POST to SP's "request token"
| URL. |
|--------------------------------------------->|
| |
| |
| 1.1. SP issues uRT and Token Secret to |
| consumer. |
|< ---------------------------------------------|
| |
| |
| |
| 1.2. User authenticates with the Service |
| Provider (optional, methods vary, realization|
| is out of scope) |
|<============================================>|
| 3. User grants or declines permission |
| for the Service Provider to issue Access |
| Token. |
| |
| |
| |
| |
| 4. Service Provider authorizes the uRT to be |
| exchanged for an Access Token and secret. |
|< ---------------------------------------------|
| |
| |
| |
| 5. Consumer exchanges the uRT and secret |
| for an Access Token and Secret. |
|--------------------------------------------->|
|< ---------------------------------------------|
| |
| |
| |
| 6. Consumer uses the Access Token, Access |
| Secret, Consumer Key, and Consumer Secret |
| to make authenticated request(s) to the Service
| Provider |
|<============================================>|
| . |
| . |
| . |
| . |
| . |
| . |
| |
Average Rating: 4.9 out of 5 based on 156 user reviews.