Some colleagues (Josh Howlett, Leif Johansson, RL “Bob” Morgan) and I had the good fortune to help the MIT Kerberos Consortium (MITKC) with some analysis and strategy planning for the (broad) topic of “Kerberos and the Web”, during this last Fall 2008. The main deliverables of this project are this document..
Towards Kerberizing Web Identity and Services
http://kerberos.org/software/kerbweb.pdf
..and this presentation..
Kerberos for the Web: Current State and Leverage Points
http://kerberos.org/events/Board-11-3-08/4-KerberosandWeb.pdf
..given at the MITKC’s Financial Services Security Summit and MIT Kerberos Consortium Executive Advisory Board Meeting last Fall.
Of course, these documents may not make much sense if one doesn’t know what Kerberos is, so if that’s the case, this brief tutorial ought to be helpful, as well as the Kerberos entry on Wikipedia. Additionally, the MITKC has published a series of Kerberos whitepapers outlining Kerberos’ role(s) in the Big Picture of information systems in general, as well as various best practices.
That said, the MITKC’s announcement of the document provides overall rationale for their Kerberos-on-the-Web project. They have also established a new public mailing list for technical discussions on this topic.
Additionally, here’s the salient portions of the paper’s abstract..
Today authentication and authorization are addressed in an incoherent, and often site-specific, fashion on the Internet and the Web specifically. This situation stems from many factors including the evolution, design, implementation, and deployment history of HTTP and HTTP-based systems in particular, and Internet protocols in general.
Kerberos is a widely-implemented and widely-deployed authentication substrate with a long history in various communities and vendor products. Organizations that currently use Kerberos as a key element of their infrastructure wish to take advantage of its unique benefits while moving to Web-based systems, but have had limited success in doing so. …
In this paper we outline the evolution of Web Identity and Services and describe the issues surrounding this complex landscape. These issues are captured within a set of more specific requirements that are deemed necessary to satisfy the relevant stakeholders; these requirements are then framed within the context of some general use cases. We then propose and describe a number of activities that leverage Kerberos to realize these improvements, and present an overall strategy and architectural model for working towards a more cohesive and widely deployed Kerberos-based Web authentication infrastructure.
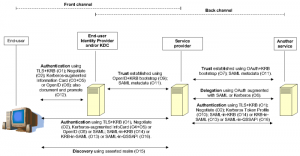
Casual readers may find the section entitled A Short History of Web Identity and Services interesting, while those desiring the gory details as well as the identified opportunities will benefit from reading the entire paper. Here’s the overall summary illustration..
In concluding, we recommend that in conjunction with developing an overall strategy and architecture with stakeholders, that the MITKC ought to initiate at least these activities..
- Specify the use of Kerberos with TLS
- SAML-in-Kerberos: Extend Kerberos to permit the inclusion of a SAML assertion in KDC issued authorization data
- Kerberos-in-SAML: SAML profile supporting the generation of SAML assertions containing Kerberos tickets
- Update WS-Security Kerberos Token Profile specification
- Leverage SAML metadata to enable large-scale Kerberos cross-realm communities”), and
- Investigate, document and promote existing methods of using Kerberos to authenticate against a SAML identity provider
Discussion of this paper and the MITKC’s overall Kerberos-and-the-Web project occurs on the (new) mitkc-web@mit.edu mailing list. Feel free to subscribe and join in.